The TCP/IP model is a layered framework in networking that explains how data is communicated between devices on a network. This model uses standard protocols to ensure data transmission is reliable and efficient.
Introducing the TCP/IP Model
The TCP/IP model is defined as a four-layer architecture, consisting of the following layers:
- Application Layer
- Transport Layer
- Internet Layer
- Network Access Layer
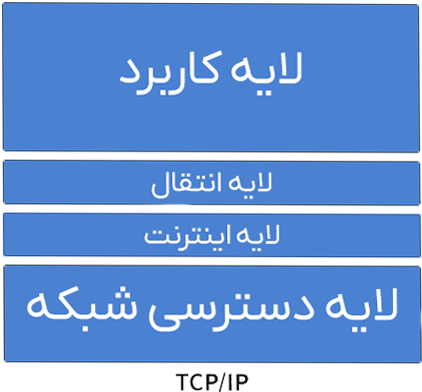
This model is standardized by RFC 1122, and its structure and behavior are described in this document. The TCP/IP model is preferred over the seven-layer OSI model due to its simplicity and practicality, and is known as the primary framework of the internet and modern network systems.
Layers of the TCP/IP Model
Application Layer
The Application Layer is the highest layer in the TCP/IP model and is considered the closest layer to the end-user. This layer provides an interface between user applications (such as web browsers, email clients, file-sharing tools) and the lower layers of the network.
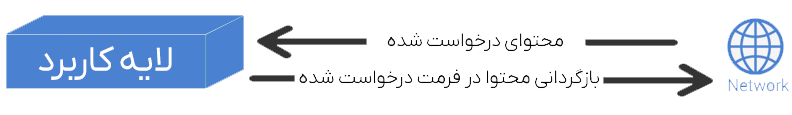
The main tasks of this layer include:
- Providing a communication bridge between user applications and underlying layers
- Supporting protocols such as HTTP, FTP, SMTP, and DNS
- Managing data formatting so that information is understandable to both sender and receiver
- Providing encryption services for secure communications
Transport Layer
The Transport Layer is responsible for ensuring reliable and efficient data delivery between devices, and manages tasks such as data segmentation, sequencing, and retransmission of lost packets.
Functions of this layer:
- Segmentation and Reassembly: Dividing large messages into smaller packets and reassembling them at the destination
- Reliable Delivery and Error Management: Error checking and retransmitting lost data using TCP
- Fast Communication: Providing connectionless and low-latency delivery using UDP
- Flow Control: Preventing the receiver from being overwhelmed by regulating the data flow
- Multiplexing: Using port numbers to allow multiple applications to share the network simultaneously
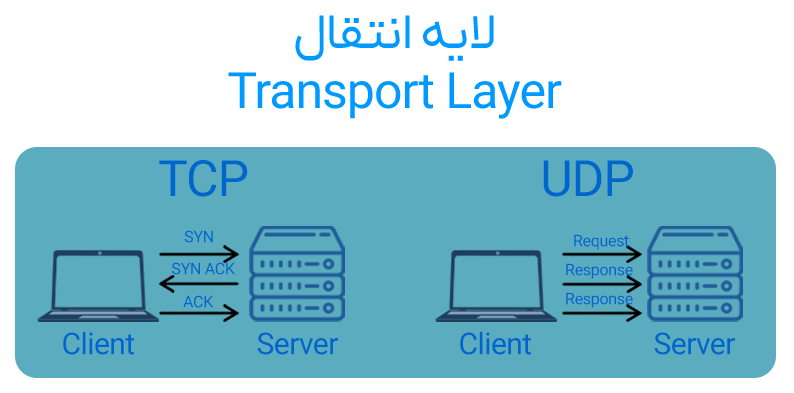
This layer consists of two fundamental protocols:
TCP (Transmission Control Protocol), which is used for communications requiring accuracy and reliability, and provides features such as error checking, retransmission of lost packets, sequential delivery, and connection-oriented communication.
UDP (User Datagram Protocol) is used for applications where speed is more important, and it is simpler and faster than TCP, but does not guarantee delivery.
Internet Layer
This layer is responsible for logical addressing, packetizing, and routing packets so that data can reach its correct destination through different networks.
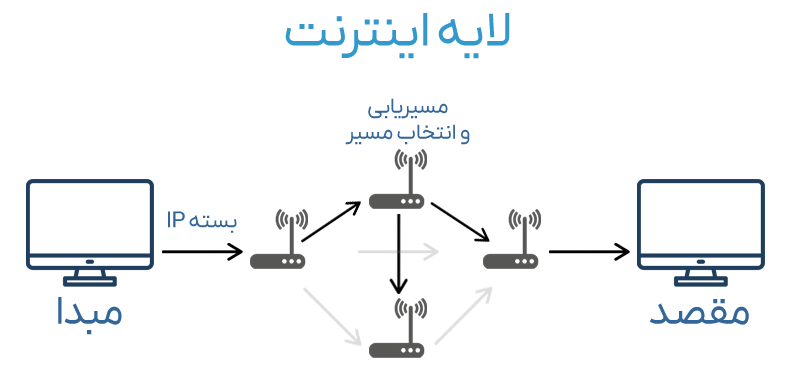
The main tasks of this layer include:
- Logical Addressing: Assigning IP addresses to identify sender and receiver devices
- Packet Routing: Determining the best path for data to travel across the network
- Fragmentation and Reassembly: Dividing large packets into smaller packets and reconstructing them at the destination.
- Protocol Support: Utilizing IP as the primary protocol, along with supporting protocols such as ICMP and ARP.
Network Access Layer
This layer is responsible for the physical transmission of data through network hardware (cables, switches, wireless communications). It manages how data is formatted for the transmission medium and ensures it reaches the next device along the path.
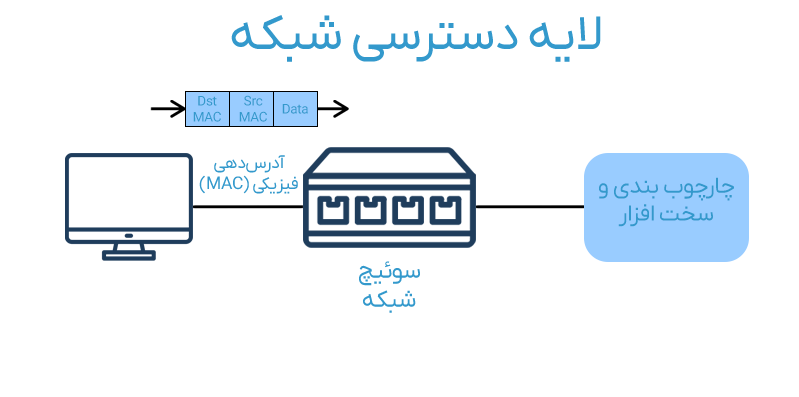
The tasks of this layer include:
- Physical Transmission: Sending and receiving raw bits over physical media such as Ethernet cables, fiber optics, or Wi-Fi.
- Framing: Organizing data into frames for correct transmission.
- Error Detection: Identifying transmission errors using checksums or CRC (Cyclic Redundancy Check).
- MAC Addressing: Utilizing hardware addresses to identify devices within a network segment.
- Access Control: Managing how the transmission medium is shared among multiple devices.
How the TCP/IP Model Works
When Sending Data (From Sender to Receiver)
In the TCP/IP model, when data is sent:
- Application Layer: The relevant software creates the data and delivers it to the next layer.
- Transport Layer: The data is divided into smaller segments, and TCP/UDP adds the necessary control information.
- Internet Layer: Each segment is placed into packets with IP addresses for routing.
- Network Access Layer: The packets are converted into frames suitable for the physical medium and transmitted.
When Receiving Data (At the Destination)
When data is received at its destination:
- Network Access Layer: Frames are received from the physical medium and error checking is performed.
- Internet Layer: Frames are decapsulated and packets are forwarded to the upper layer using IP addresses.
- Transport Layer: Segments are reassembled, and errors are corrected if TCP is used.
- Application Layer: The complete data is delivered to the appropriate software.
Advantages of the TCP/IP Model
The TCP/IP model has the following advantages:
- Wide applicability: It forms the basis of the internet and modern networks.
- Platform independence: It can be implemented on various hardware and operating systems.
- Reliable communication: TCP provides error checking, delivery confirmation, and data integrity.
- Scalability: It supports networks ranging from small setups to the global internet.
Limitations of the TCP/IP Model
Some of the limitations of this model include:
- Complexity for Beginners: Fully understanding all the protocols can be difficult.
- Lack of Strict Layering: Unlike the OSI model, the layers in TCP/IP are not strictly defined.
- Data Overhead: The reliable features of TCP can create additional overhead.
- Security Limitations: The initial design of the model did not have strong security and requires additional protocols.
- Limited Multimedia Support: The initial design was for data, not optimized for video/audio.
Why Use TCP/IP Over the OSI Model
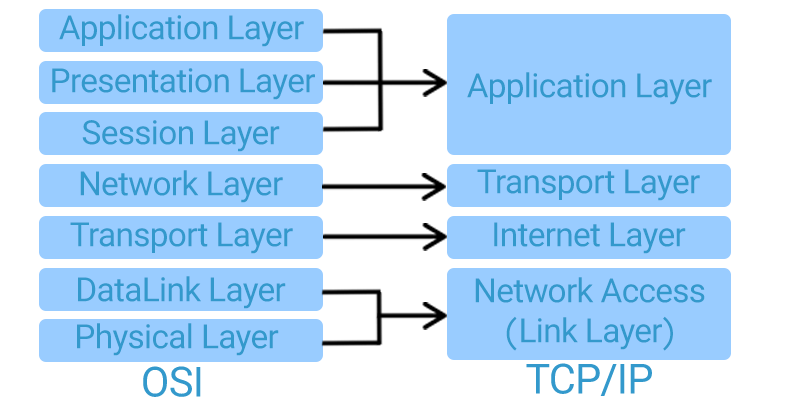
TCP/IP is preferred over the OSI model due to its simplicity, practical application, and widespread implementation in real-world networks and the internet. Key differences include:
- Simpler Structure: TCP/IP consists of 4 layers compared to 7 layers in OSI.
- Protocol-Based Design: TCP/IP is built upon actual protocols, while OSI is more of a theoretical framework.
- Flexibility and Robustness: TCP/IP functions well across various hardware and networks.
- Open Standard: TCP/IP is open and not controlled by a single organization.
- Practical Application vs. Conceptual Model: OSI is primarily educational, whereas TCP/IP is used in practice.
